
- Home
- Cybersecurity Tips
- 9 Types of Cyber Crimes: A Guide to Stay Protected
Cybercrime, in its simplest form, refers to any illegal activity that uses a computer, network, or other digital devices as its primary tool. With our increasing reliance on the digital world – for communication, finance, entertainment, and more – the opportunities for these types of cyber crimes are also multiplying.
To grasp the magnitude of the problem, consider this: cybercrime is predicted to inflict damages totaling USD 9.5 trillion globally in 2024, which would make it the world’s third-largest economy after the U.S. and China. The impacts of cybercrime are far-reaching, affecting individuals, businesses, and governments alike. Let’s explore the different types of cybercrimes and understand how we can protect ourselves.
If you’re looking to strengthen your defenses against cybercrime, reach out to Class IV. Our team of experts can help you assess your vulnerabilities and implement strategies to safeguard your digital assets!
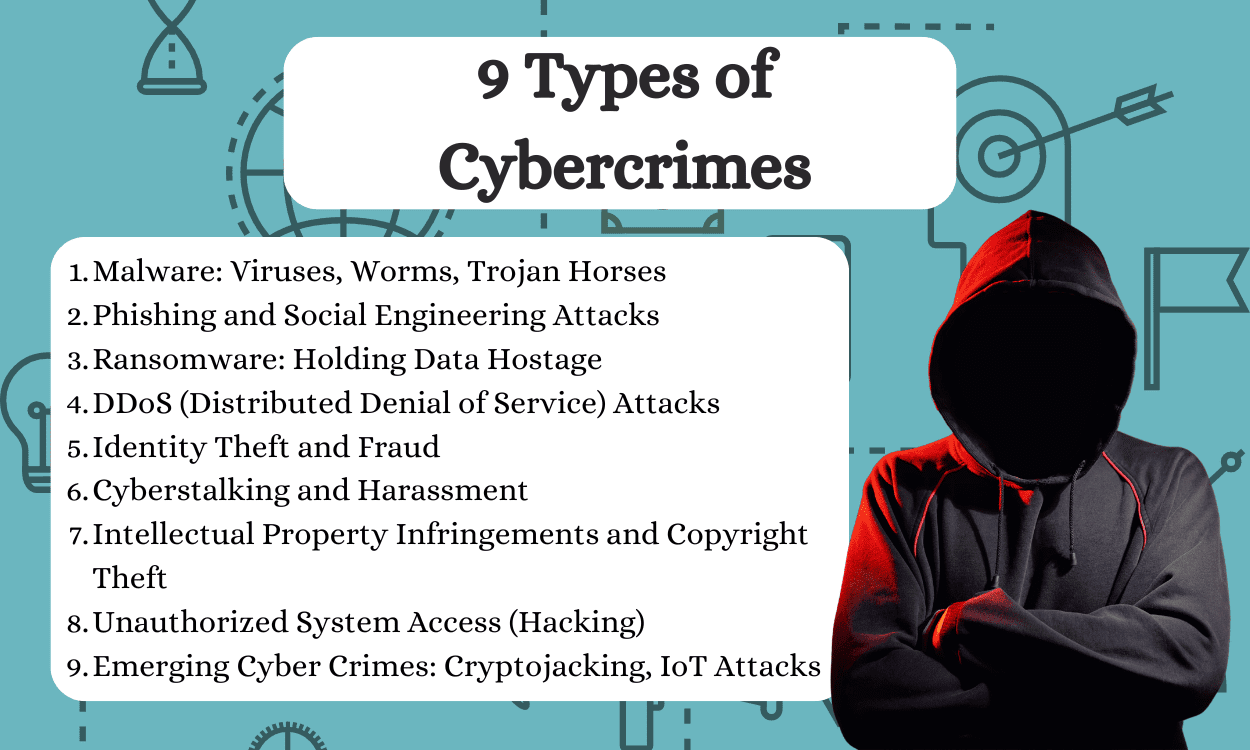
9 Types of Cybercrimes
While technology brings convenience and connectivity, it also opens doors for malicious actors to exploit vulnerabilities. These malicious acts are broadly categorized as cyber crimes, posing significant threats to individuals, businesses, and governments globally. Let’s explore nine prevalent types of cyber crimes:
Malware: Viruses, Worms, Trojan Horses
Malware, encompassing viruses, worms, and Trojan horses, is a cornerstone of many cybercrime types. Delivered primarily through emails—a staggering “94% of malware is delivered via email“— these malicious software programs infiltrate devices to wreak havoc. Viruses attach themselves to legitimate software, replicating and spreading rapidly. Worms, on the other hand, self-replicate and spread across networks, exploiting vulnerabilities to compromise systems. Trojan horses disguise themselves as harmless applications, tricking users into granting them access only to unleash their malicious payload once inside.
Phishing and Social Engineering Attacks
Have you ever received an email that seemed too good to be true? That’s probably a phishing attempt. Phishing and social engineering attacks prey on human vulnerability, manipulating individuals into divulging sensitive information. Phishing emails often mimic legitimate organizations, enticing users to click on malicious links or provide login credentials. With “over 75% of targeted cyberattacks starting with an email in 2024“, phishing remains a primary vector for cybercrime, highlighting the importance of vigilance and skepticism.
Ransomware: Holding Data Hostage
Ransomware is malicious software that encrypts victims’ files, holding their data hostage. Perpetrators then demand a ransom, often in cryptocurrency, in exchange for the decryption key. The impact of ransomware attacks can be crippling, leading to data loss, financial damage, and reputational harm. Consider this: “Ransomware continues to be the most prevalent form of malware, involved in nearly 70% of malware-related breaches.“
DDoS (Distributed Denial of Service) Attacks
Imagine a digital traffic jam, effectively shutting down a website or online service. That’s the essence of a DDoS (Distributed Denial of Service) Attack. By overwhelming a target server with a flood of traffic from multiple sources, attackers can render websites and online services inaccessible to legitimate users. DDoS attacks can disrupt business operations, resulting in financial losses and reputational damage.
Identity Theft and Fraud
In an era where personal information holds immense value, identity theft and fraud have become increasingly prevalent cybercrime examples. Cybercriminals steal personal information, such as social security numbers, credit card details, and login credentials, to assume victims’ identities. They then exploit this stolen information to make unauthorized purchases, open fraudulent accounts, or access and manipulate existing accounts, leading to significant financial and emotional distress for victims.
Cyberstalking and Harassment
The internet, while connecting people globally, also provides anonymity, which unfortunately enables cyberstalking and harassment. These types of cybercrimes involve using electronic communications to stalk, harass, threaten, or intimidate an individual or group. From persistent online harassment to defamation and the spread of malicious rumors, cyberstalking can have severe emotional and psychological impacts on victims.
Intellectual Property Infringements and Copyright Theft
The digital age has made it easier than ever to create, share, and distribute copyrighted material. However, it has also opened avenues for intellectual property infringements and copyright theft. This category of cybercrime involves the unauthorized reproduction, distribution, or use of copyrighted works, including music, movies, software, and literary works. These infringements not only harm creators and copyright holders but can also stifle innovation and creativity.
Unauthorized System Access (Hacking)
Unauthorized system access, commonly referred to as hacking, involves illegal entry into computer systems, networks, or devices. Hackers exploit vulnerabilities to access sensitive data, disrupt operations, or take control of systems. Their motivations can range from personal gain, such as financial profit or data theft, to causing widespread disruption or promoting political agendas.
Emerging Cyber Crimes: Cryptojacking, IoT Attacks
As technology rapidly evolves, so too do the methods employed by cybercriminals. Emerging cyber crimes, such as cryptojacking and IoT attacks, are gaining traction. Cryptojacking involves hijacking unsuspecting users’ computing power to mine cryptocurrencies without their knowledge or consent. IoT attacks target Internet of Things (IoT) devices, such as smart home devices and wearable technology, exploiting vulnerabilities to steal data, disrupt services, or even cause physical harm.
Battling Cybercrime: Prevention, Protection, and Response Measures
The pervasiveness of technology has brought about an unfortunate increase in cybercrime. From phishing scams to ransomware attacks, cybercriminals’ methods are becoming increasingly sophisticated. However, by understanding the importance of cybercrime prevention, individuals and organizations can take proactive steps to mitigate these risks. Cybercrime and prevention go hand in hand—one cannot exist without the other. Therefore, exploring effective cybercrime solutions is paramount in our interconnected world.
Educational Awareness and Training for Cyber Hygiene
Believe it or not, human error is a significant contributing factor to cybercrime. A study revealed that a staggering “88% of cybersecurity breaches are caused by human error.” This highlights the critical need for educational awareness and training programs. By educating individuals about common cyber threats, such as phishing emails, social engineering tactics, and password security, we can empower users to identify and avoid potential risks.
Implementing Robust Security Protocols and Infrastructure
Robust security protocols and infrastructure are non-negotiables in the fight against cybercrime. This encompasses a multi-layered approach that includes:
- Strong Passwords and Multi-Factor Authentication: I cannot stress enough how important it is to use strong, unique passwords for all your online accounts and implement multi-factor authentication whenever possible.
- Regular Software Updates: Regularly updating your operating systems, applications, and security software is crucial for patching vulnerabilities that cybercriminals could exploit.
- Firewall and Intrusion Detection Systems: Employing firewalls and intrusion detection systems can act as a barrier against unauthorized access to your networks and devices.
Legislative Measures and International Cooperation Against Cybercrime
Cybercrime operates across borders, making it crucial to establish comprehensive legislative measures and foster international cooperation. Governments and law enforcement agencies play a vital role in enacting laws that criminalize cybercrime activities. For instance, I find that the increasing number of cyber attacks, with “the average number of cyber attacks per organization per week reaching 1,636 in the second quarter of 2024,” necessitates a globally unified approach. Additionally, fostering collaboration between countries can facilitate the sharing of information, intelligence, and best practices to combat cybercrime effectively.
Conclusion
As we navigate the complexities of our digital world, understanding the various types of cyber crimes is crucial for safeguarding ourselves and our information. From malware and phishing attacks to identity theft and cyberstalking, the threats are diverse and evolving. By remaining vigilant and informed, we can take proactive steps to protect our personal and financial information. Implementing strong security measures, practicing skepticism when encountering unsolicited communications, and staying up-to-date on the latest cybersecurity trends are all essential strategies. Remember, awareness is your first line of defense. Stay safe online and protect your digital life today! For more on how to enhance your cybersecurity practices, be sure to check out our other resources and articles.
For more on how to improve your cybersecurity practices, be sure to check out our other resources and articles. Additionally, if you’re looking to take your cybersecurity knowledge to the next level, consider partnering with Class IV. Our expert team offers tailored solutions to enhance your IT infrastructure and safeguard your business from cyber threats. Don’t wait—reach out to us today to discuss how we can help protect your digital assets!


